Monday, 24 February 2020
100 Questions
100 Questions
1.
Mention all the different views of O.S.
2.
List the different types of O.S. and compare them
3.
What is Distributed O.S.? Mention its advantages and disadvantages
4.
Explain what is Real Time O.S. and how many types are there, explain.
5.
What is multiprogramming ? Explain with its advantages.
6.
Name the different system components, mentioning the function of each.
Define System Call.
7.
What are system programs and their functions ?
8.
What are different types of system structures, compare them.
9.
What is layered approach? Explain.
10. What is a virtual machine?
How it is useful in a system?
11. Explain the client-server
architecture.
12. Define what is a process.
Explain the different states of a process.
13. What is a PCB? Why is it
required?
14. Why a process scheduling is
necessary in a system?
15. How many types of queues are
required to be maintained during scheduling? Explain.
16. What is a medium term
scheduler?
17. Why a long term scheduler
cannot be used for CPU scheduling?
18. Explain the need for context
switching with respect to processes scheduling.
19. How many operations a
process consists of ? explain..
20. Why co-operating nature of
processes is required in a system? How is it useful?
21. What is the need for thread
concept in a system? How is it different
from a process?
22. How the co-operating processes
can establish communication link among them?
23. What is an IPC? Why it is
required in a system?
24. Give an example of message
based operating system and discuss.
25. What are the different types
of queues present in a system?
26. Explain the need for a
proper job mixing before scheduling.
27. Give a comparison of all the
CPU scheduling algorithm
28. Consider the given job
mixing
a.
Process BT Priority
b.
P1 8 2
c.
P2 2 1
d.
P3 3 3
e.
P4 5 4
f.
Processes are arrived in P1, P2, P3, P4 order all at time 0.
29. With a Gnatt chart, illustrate
the execution of these processes using FCFS, SJF, non-preemptive priority and
RR (Quantum=2) scheduling.
30. Find the turnaround time for
all scheduling methods in part(a)
31. Find out the wait time for
all scheduling methods in part(a).
32. Find out which method results
in minimum average wait time.
33. Explain how quantum
selection in RR scheduling affects scheduling.
34. When multilevel feedback
queue scheduling is required. Explain.
35. Compare the 3 scheduling
algorithm evaluation methods. Justify which is more accurate.
36. Why process synchronization
is requires in a system? Justify your answer.
37. What is a critical region,
and what do you men by critical region problem. ?
38. Write an algorithm to
overcome all the problems of critical section; explaining how each problem is
met.
39. Is it possible to use
hardware instructions to solve critical region problem ? Explain.
40. What is semaphore ? Name its
types. Why it is required?
41. What are classical
synchronization problems and how they are useful for a system? Explain.
42. How can you use high level
constructs to achieve synchronization solutions? Explain. Is it possible to
overcome all the problems?
43. What is a monitor? How it is
used to implement synchronization solution ?
44. The sleeping-barber problem
– A barber shop consists of a waiting room with ‘n’ chairs and the barber room
consists barber chair. If there are no
customers to be server, barber goes to sleep. If a customer enters the shop and
all the chairs are occupied, customer leaves the shop. If the barber is busy, but chairs are available,
then customers sits in the free chairs. If the barber is asleep, customer wakes
up the barber. Write a program
to co-ordinate the barber and the customer.
45. Write a monitor to implement
the barber-customer problem as in Q9.
46. What are deadlocks?
47. Which are the four
conditions that hold deadlock?
48. What are resource allocation
graphs? Explain.
49. Discuss the different ways
of deadlock management.
50. Explain how deadlocks may be
prevented.
51. What do you understand by
deadlock avoidance?
52. Discuss safe state of a
system.,
53. Explain how resource
allocation graphs may be used to find safe or unsafe state of a system.
54. Discuss the Banker’s
algorithm.
55. Write short note on the
following
a.
Deadlock Detection b) Deadlock recovery
56. Explain what is address
binding.
57. Give the difference between
a.
Logical and Physical Addressing
b.
Internal and External Fragmentation
58. Explain the different
allocation algorithms.
59. How is pages different from
partitions? Explain with example.
60. What is segmentation? How is
it useful?
61. Explain MULTICS systems.
62. What is virtual memory and
its advantages?
63. Why page replacement
algorithm is required? Explain the types with examples. Compare them.
64. What is “Allocation of
frames” and discuss the criterions?
65. Discuss the demand
segmentation.
66. Compare the file with other
storage medias.
67. Some system keep track of
the file type and others leave it to the user or may not implement multiple
file types. Which is better among the three mentioned above?
68. Explain the open and close
operations purpose.
69. Describe the protection problem
that could arise and suggest a scheme of dealing with such problems. How would
you specify this problem in Unix?
70. Consider a system where free
space is kept in a free space list.
a.
Suppose of the pointer to that free space list is lost, can the system
reconstruct the free-space list. Explain
b.
Give a scheme to ensure that the pointer is never lost as memory fails.
71. Name the problem that could
occur when file system needs to be mounted simultaneously iat more than one
location in a system.
72. Why the bit map for file
allocation cannot be kept on main memory.
73. Explain internal and
external fragmentation on a storage device with respect to file system.
74. Explain how caches help in
performance improvement and why system cannot use larger cache, even though
they are useful.
75. When is it advisable to use
a RAM disk than a disk cache.
76. What is backup and why it is
required? Explain with an example.
77. What is the need for a
secondary storage in a system and how it is structured?
78. Why is disk scheduling
required? Justify your answer.
79. Discuss the different
scheduling techniques with respect to optimization achieved.
80. Assuming a disk drive with
1000 cylinders, numbered from 0-999, abd drive currently serving a request at
cylinder 200 and queue of pending requests in FIFO order as
i.
86, 913, 948, 1320, 600, 755, 849, 525, 356
b.
Calculate the total distance in cylinders the arm moves to satisfy
pending requests for the following disk-scheduling methods.
c.
(i) FCFS (ii)
SSTF (iii) SCAN
(iv) C-SCAN
81. What are the trade-offs
involved in rereading code pages from the file system versus using swap space
to store them.
82. Explain why swap-space is
needed in a system and its relative points.
83. In what way the operating
system is responsible for disk management. Explain with different aspects.
84. How do you improve disk
reliability and why it is needed?
85. Compare the secondary
storage with primary storage system with respect to all the necessary aspects.
86. Differentiate between
capability and access lists.
87. Discuss the features needed
in a system for efficient capability manipulation. And justify whether it can
be used in memory protection.
88. If a shared stack is used
for parameter passing, what kind of protection problem may arise.
89. Explain why is it difficult
to protect a system, where the users are allowed to perform their own I/O.
90. List the relative merits
with respect to enforcement based on kernel and provided by a compiler.
91. Why security is must in a
system? What are security problems discuss ?
92. How many password types are
there name and explain them.
93. When Trojan horse is needed.
94. What is worms and viruses in
a system?
95. Explain encryption in a
system.
96. Write the main features of
Windows NT architecture.
97. What are the main design
principles? Discuss.
98. With a neat block diagram
explain the different system components in brief.
99. Explain the virtual memory
concept in Windows NT with neat figure.
100. Name the different
environmental subsystems and explain them.
101. How Recovery is achieved in
Windows NT file system?
102. Name the different protocols
supported by Windows NT networking and explain.
103. How is inter-process
communication achieved in Windows NT System.
104. How is object sharing
implemented in Windows NT system.
OS Study Material
Text Book : Operating System Concepts
Authors: Avi Silberschatz, Peter Baer Galvin, Greg Gagne
PPT and PDF of the Chapters( as listed in below table )
| Chapter | Powerpoint | Last Updated |
| Part 1: Overview | ||
| 1. Introduction | Sep 21, 2013 | |
| 2. Operating-System Structures | Sep 21, 2013 | |
| Part 2: Process Management | ||
| 3. Processes | Sep 21, 2013 | |
| 4. Threads | Sep 21, 2013 | |
| 5. Process Synchronization | Nov 28, 2013 | |
| 6. CPU Scheduling | Sep 21, 2013 | |
| 7. Deadlocks | Sep 21, 2013 | |
| Part 3: Memory Management | ||
| 8. Main Memory | Sep 21, 2013 | |
| 9. Virtual Memory | Sep 21, 2013 | |
| Part 4: Storage Management | ||
| 10. Mass-Storage Structure | Sep 21, 2013 | |
| 11. File-System Interface | Sep 21, 2013 | |
| 12. File-System Implementation | Sep 21, 2013 | |
| 13. I/O Systems | Sep 21, 2013 | |
| Part 5: Protection and Security | ||
| 14. Protection | Sep 21, 2013 | |
| 15. Security | Sep 21, 2013 | |
| Part 7: Advance Topicss | ||
| 16. Virtual Machines | Sep 21, 2013 | |
| 17. Distributed Systems | Sep 21, 2013 | |
| Part 6: Case Studies | ||
| 18. The Linux System | Sep 21, 2013 | |
| 19. Windows 7 | Sep 21, 2013 | |
| 20. Historical Perspective | ||
| Appendices | ||
| A. BSD UNIX | Sep 21, 2013 | |
| B. The Mach System | ||
Editor of this Blog Acknowledges: Text Book Operating System Concepts and
Authors - Avi Silberschatz, Peter Baer Galvin, Greg Gagne
Note: Readers are suggested to read Copyright Note of this text book at the given link
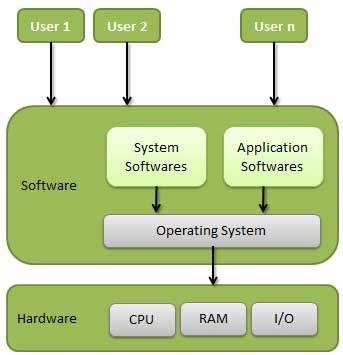
Operating System
Operating System
A System program that controls and Coordinate all activities of Computer System providing an interface to the user

Can be Visualized in details as below figure
Subscribe to:
Comments (Atom)
-
Operating System Previous Years University Exam Question Papers Please click here to access the question papers
